| |
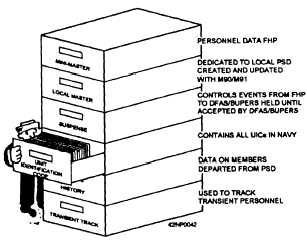
Figure 15-3.—Files contained in the source data system.
The FHPs interface with central host processors
(CHPs) located at BUPERs and DFAS - Cleveland
Center. CHPs are responsible for providing interim
and/or final disposition for all SDS events received.
When events are received from the FHP by the CHP, the
CHP processes these events according to the type of
events—personnel or payroll.
Personnel events. SDS events are created for the
purpose of updating a member’s record (officer or
enlisted). The BUPERS CHP processes the event and
passes the data into either the officer or enlisted update
cycle. At this time, various edits are performed against
the data. If the data is valid, it is applied to the member’s
record and accepted feedback is provided to the FHP.
If discrepancies are found, the data is rejected. No
changes are made to the member’s master record until
analysis and changes (if required) are made at the
headquarters level or the event is sent back to the field
for resubmission. Feedback is also provided to the FHP
for data that fails MAPMIS edits.
Payroll events.
DFAS - Cleveland Center CHP
processes all payroll events. The events are entered into
the event master set to maintain an audit trail and
provide for statistical reporting. The events are then
entered into the JUMPS update cycle. The output from
the updates is then reformatted into feedback records
for the originating PERSUPPDET. Feedback ranges
from control information for accepted events to control
information and status/error codes for rejected,
recycled, or canceled events. Figure 15-4 illustrates the
flow of data to and from the PERSUPPDET and
BUPERS/DFAS - Cleveland Center.
Event Processing
When an action occurs creating a requirement for
an SDS event, it is inputted into the system by accessing
a KVDT. Following input, the event remains in the
local system until it is released by an authorized
individual. After release, the data is forwarded, via
telecommunications, to MAPMIS or JUMPS, or both,
depending on the event. If all data is accurate, it is
applied to the master files, and feedback is provided to
the originator of the system or where the document was
prepared. For each event entered into the system, a hard
copy (referred to as the substantiating document) is
printed for review and signature by the supervisor.
Depending on the event, a copy may be filed in the
member’s service record or personal financial record
(PFR). Look at figure 15-5. Here you see two petty
officers using the SDS at a PERSUPPDET.
Event Accounting
Each event entered into the system is immediately
identified by a unique sequence of numbers called a
document control number (DCN). A DCN is then
applied to every single document in order to trace them
from origin to release. Events released are assigned
ECNs to track events until they are applied to the master
record on MAPMIS or JUMPS.
Security
A critical element of the computerization of any pay
or personnel data base is security. The integrity of the
data must not be compromised. For that reason, only
selected personnel are authorized the passwords
required to access the system. Additionally, there we
many levels of access for “read only” through
manipulation of entire data bases.
Whenever tasks are completed, users are required
to “log off” the system. Logging off is important! If
the user leaves the computer terminal unattended
without logging off, another person can make
unauthorized entries. If this occurs, the person who
initially was using the system is responsible for the
unauthorized entries made. To make the system harder
for an unauthorized person to enter, the SDS has a
15-7
|